Configuring SSO With Google Using OIDC
Overview
SugarIdentity allows single sign-on authentication using Google and OpenID Connect (OIDC) so that Sugar can be integrated with a connected system using a single user ID and password. This article walks through configuring Google to allow external authentication using OpenID Connect for instances that use SugarIdentity.
For more information about external authentication methods, please refer to the following pages:
Prerequisites
- Your SugarIdentity users should be users in your organization's Google account.
- You must have an active Google account in order to complete the steps in this article.
- You must be familiar with how to set up the SSO configurations that meet your organization's needs.
- You must be a Sugar administrator to configure the OIDC settings in SugarIdentity.
Steps to Complete
Creating OIDC Application in Google
Use the following steps to create the OIDC application in Google to obtain the Client ID and Client Secret credentials:
- Navigate to the Google Developers site in your web browser.
- Sign in using the Google account under which you would like to register the application.
- Create a new project using one of the following methods:
- Click the Create Project button, enter a project name of your choice (e.g., SugarCRM OIDC), and then click "Create".
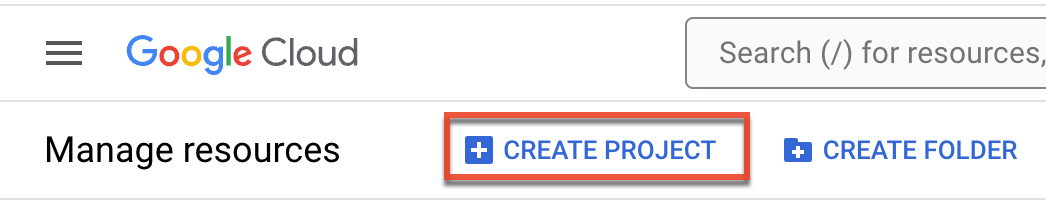
- If you do not see the Create Project button, then click "Select a project" in the navigation bar. Click "New Project" in the Select a project window, enter a project name of your choice (e.g., SugarCRM OIDC), and then click "Create".
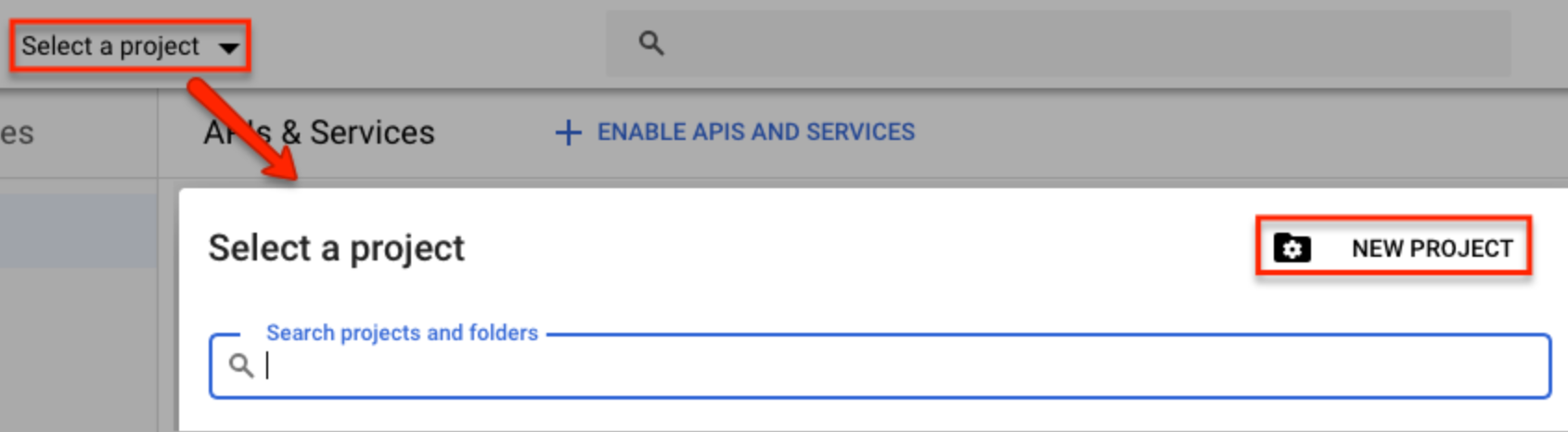
- Click the Create Project button, enter a project name of your choice (e.g., SugarCRM OIDC), and then click "Create".
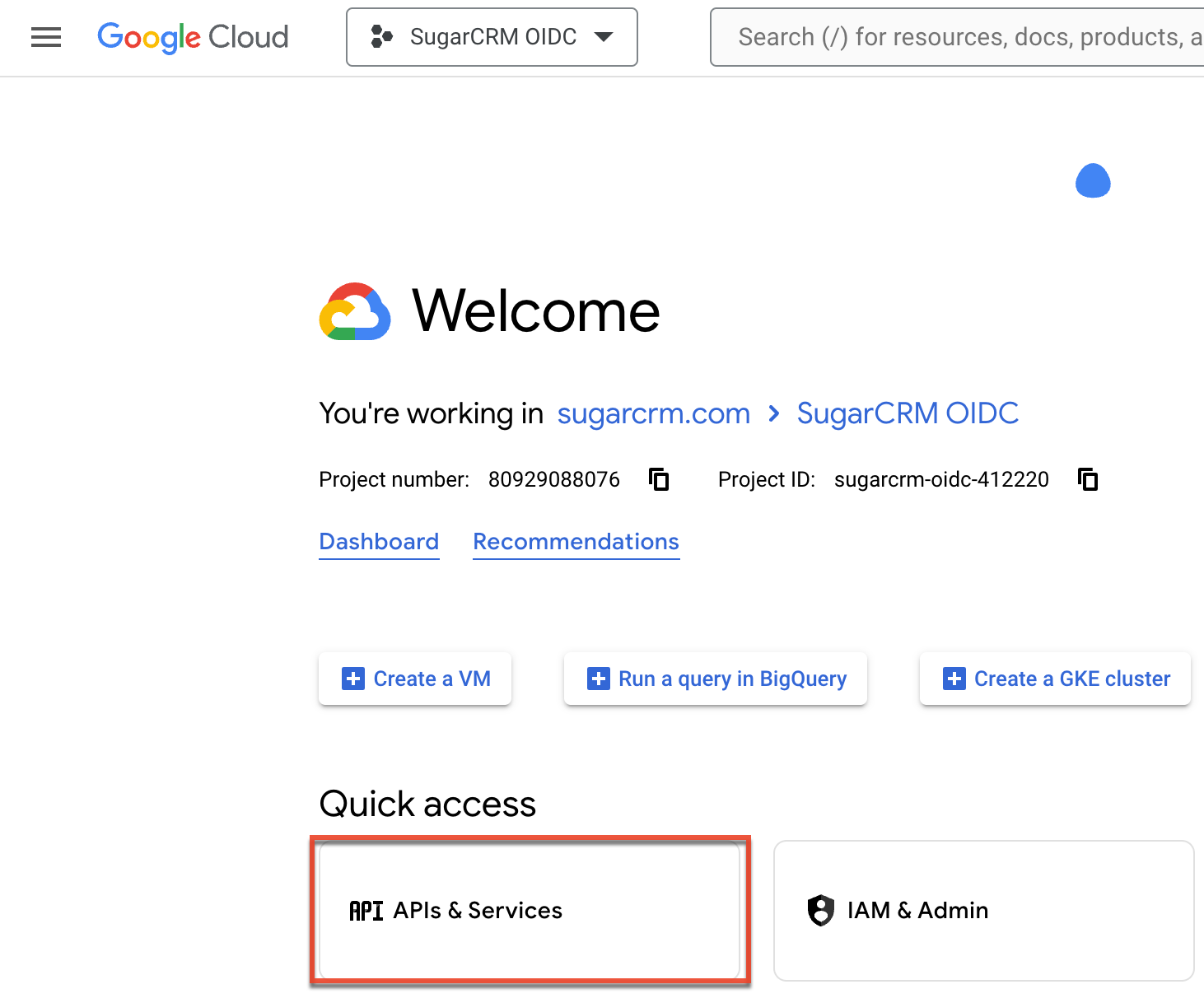
- Next, click the Google Cloud logo in the navigation bar on top, and the page will open with your newly created project selected (e.g., SugarCRM OIDC). Click "APIs & Services" under the Quick Access section, then click "Credentials" on the left tree menu on the following page.
- On the Credentials page, click "+ Create Credentials" and then select "OAuth client ID" for the credential type. If this is your first API project, please follow the steps below to configure the OAuth consent screen, otherwise skip to step 6.
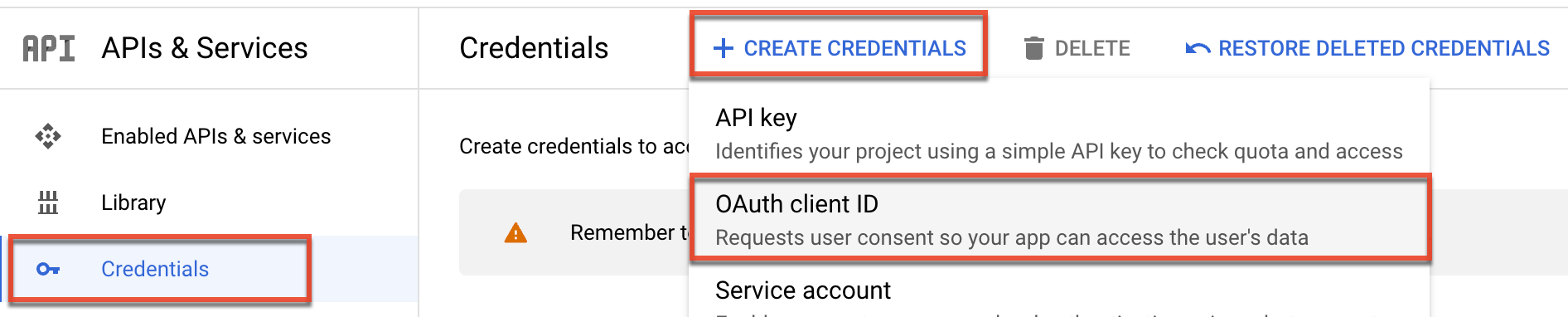
- Google will prompt you to configure the OAuth consent screen if this is your first API project. Users will see this screen when your application requests access to their private data. Click the Configure Consent Screen button.
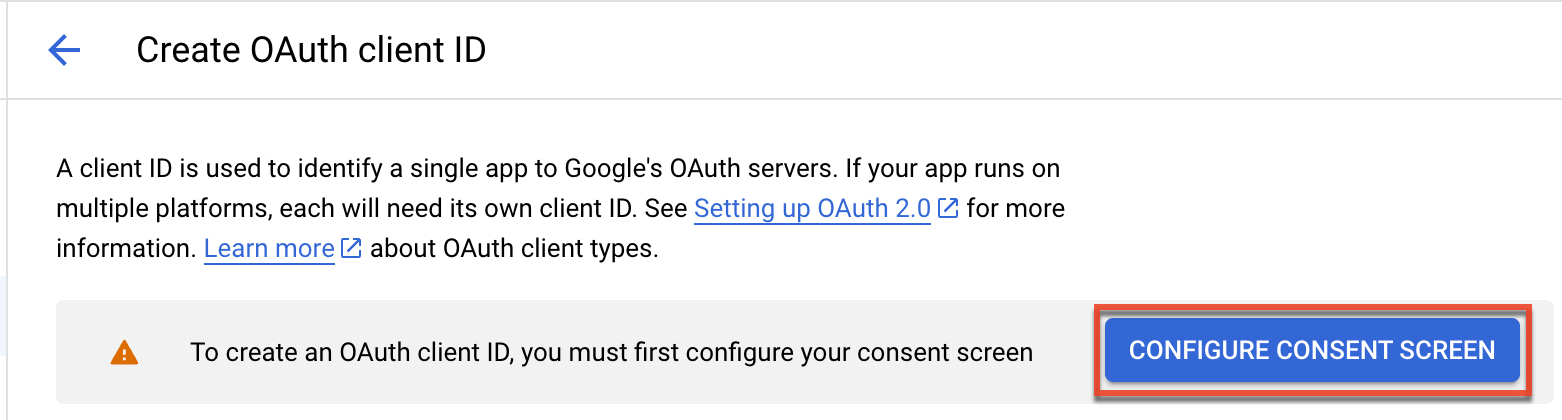
- On the OAuth consent screen, select "Internal" as the user type then click "Create". On the following screen, complete the required fields (e.g., App name, User support email), then click "Save and Continue". Complete the following screens (e.g., Scopes) accordingly. Finally, click "Credentials" on the left tree menu, click "+ Create Credentials", and select "OAuth client ID" as shown in step 5
- Google will prompt you to configure the OAuth consent screen if this is your first API project. Users will see this screen when your application requests access to their private data. Click the Configure Consent Screen button.
- Select "Web application" on the Create OAuth client ID screen then enter the Authorized Redirect URIs.
Note: Access SugarIdentity to obtain the Redirect URI value. Simply click "OIDC Settings" from the home page, then select the "Enable OIDC Authentication" option. Copy the Redirect URI value on the OIDC Settings page and paste it in the URIs field as shown below: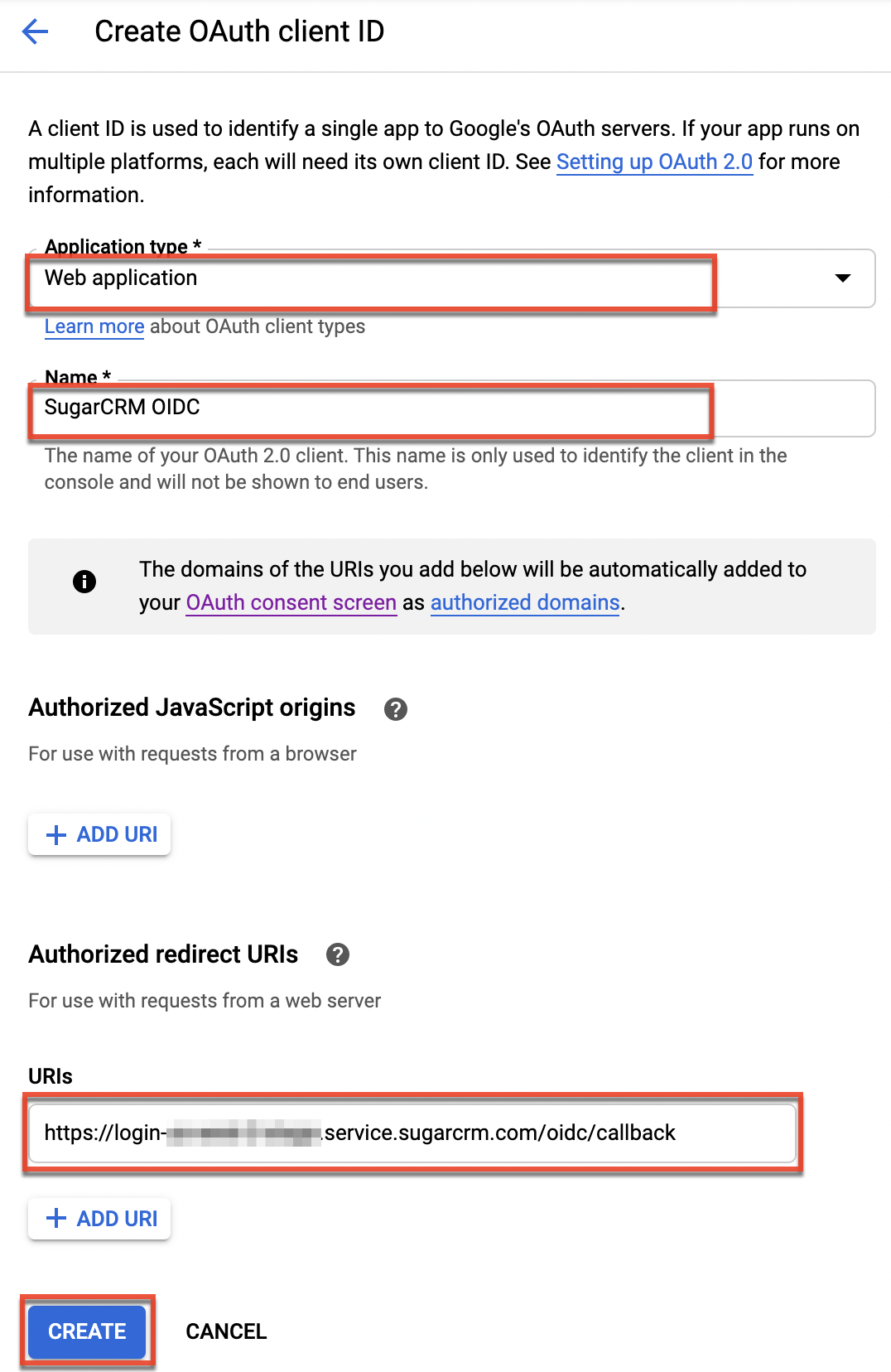
- Click "Create" to generate your unique credentials. The Client ID and Client Secret information will display in a pop-up window. Record both of these values as they are required when configuring OIDC in SugarIdentity.
Once you have obtained the Client ID and Client Secret information, navigate back to SugarIdentity to configure the OIDC authentication and complete the fields as follows:
- OIDC Server Authorization Endpoint: Enter https://accounts.google.com/o/oauth2/v2/auth.
- OIDC Server Token Endpoint: Enter https://oauth2.googleapis.com/token.
- OIDC Server Userinfo Endpoint: Enter https://openidconnect.googleapis.com/v1/userinfo.
- Client ID: Enter the Client ID obtained in step 7 above.
- Client Secret: Enter the Client Secret obtained in step 7 above.
- Scopes: Remove the "address" and "phone" scopes from the field.
Application
Once you have configured Google and completed the OIDC configuration in SugarIdentity, going forward, when a user that is provisioned in SugarIdentity navigates to Sugar they will be redirected to Google's login page to enter their login credentials. Once the user's login credentials are authenticated in Google, they will be directed back to their Sugar instance and be automatically logged in. Please note that all of the organization's users in Google will be assigned to the SugarCRM OIDC application by default once it has been created for SugarIdentity. For best practices on creating users in SugarIdentity, please refer to the SugarIdentity Guide.