Configuring SSO With Azure Using OIDC
Overview
SugarIdentity allows single sign-on (SSO) authentication using Microsoft Azure and OpenID Connect (OIDC) so that it can be integrated with a connected system using a single user ID and password. This article walks through configuring Microsoft Azure to allow external authentication using OpenID Connect for instances that use SugarIdentity.
For more information about external authentication methods, refer to the following pages:
Prerequisites
- Your organization must have an active Microsoft Azure account. For information on setting up an Azure account for your organization, please refer to their website at https://www.azure.com.
- Your SugarIdentity users should be users in your organization's Azure account.
- You must be familiar with Azure and how to set up the SSO configurations that meet your organization's needs.
- You must be a Sugar administrator to configure the OIDC settings in SugarIdentity.
Steps to Complete
Configuring Azure With SugarIdentity
Registering OIDC Application in Azure
Use the following steps to register the OIDC application in Azure and obtain the necessary credentials to configure OIDC in SugarIdentity:
- First, log in to Sugar and navigate to Admin > SugarIdentity, then click "OIDC Settings" from the home page. Place a check in the Enable OIDC Authentication box then copy the Redirect URI value as this is required to complete step 3.
Note: For Sugar versions 13.0 and lower, navigate to Admin > SugarCloud Settings.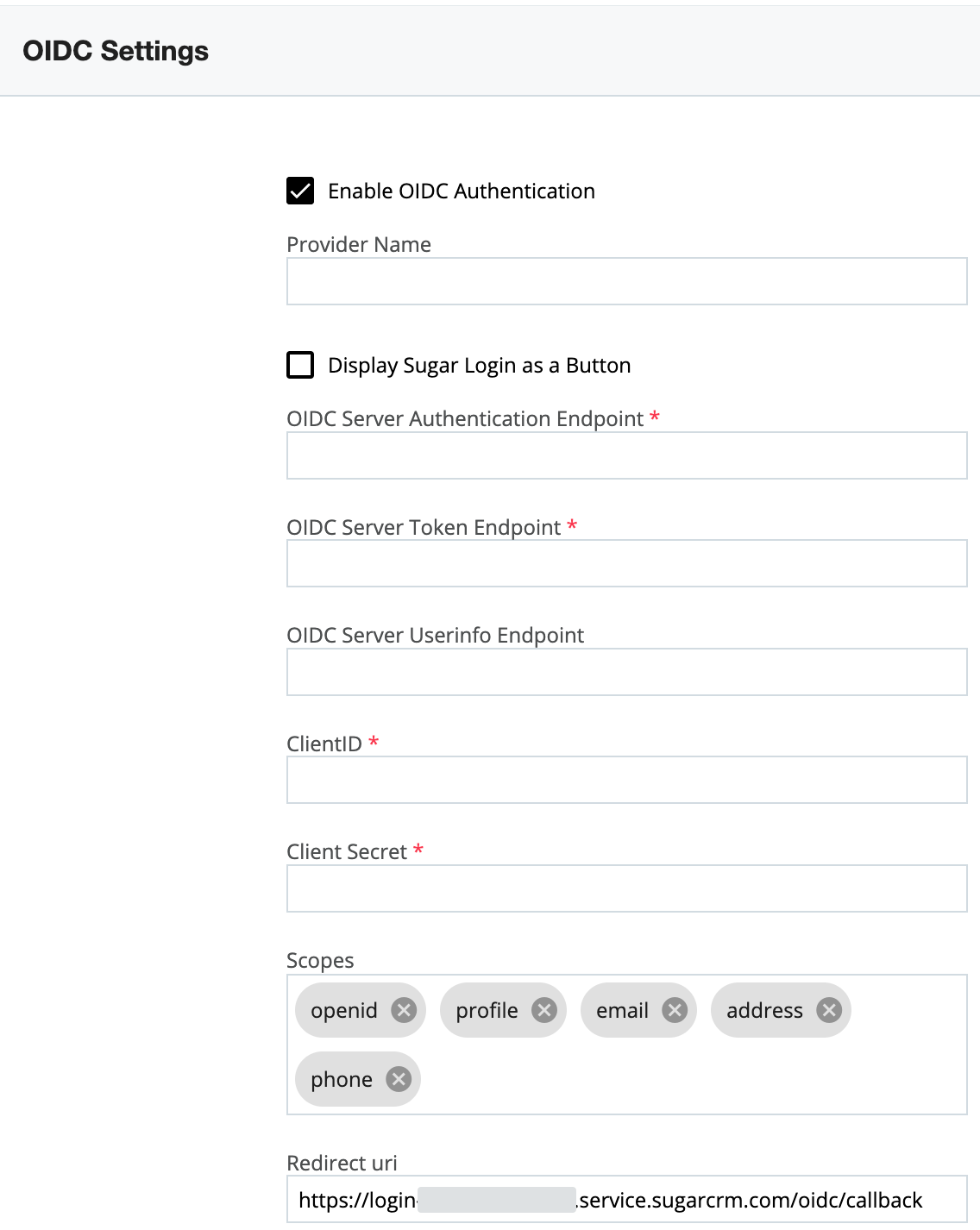
- Next, follow steps 1 - 4 in the Register a client application in Azure Active Directory article on Microsoft.
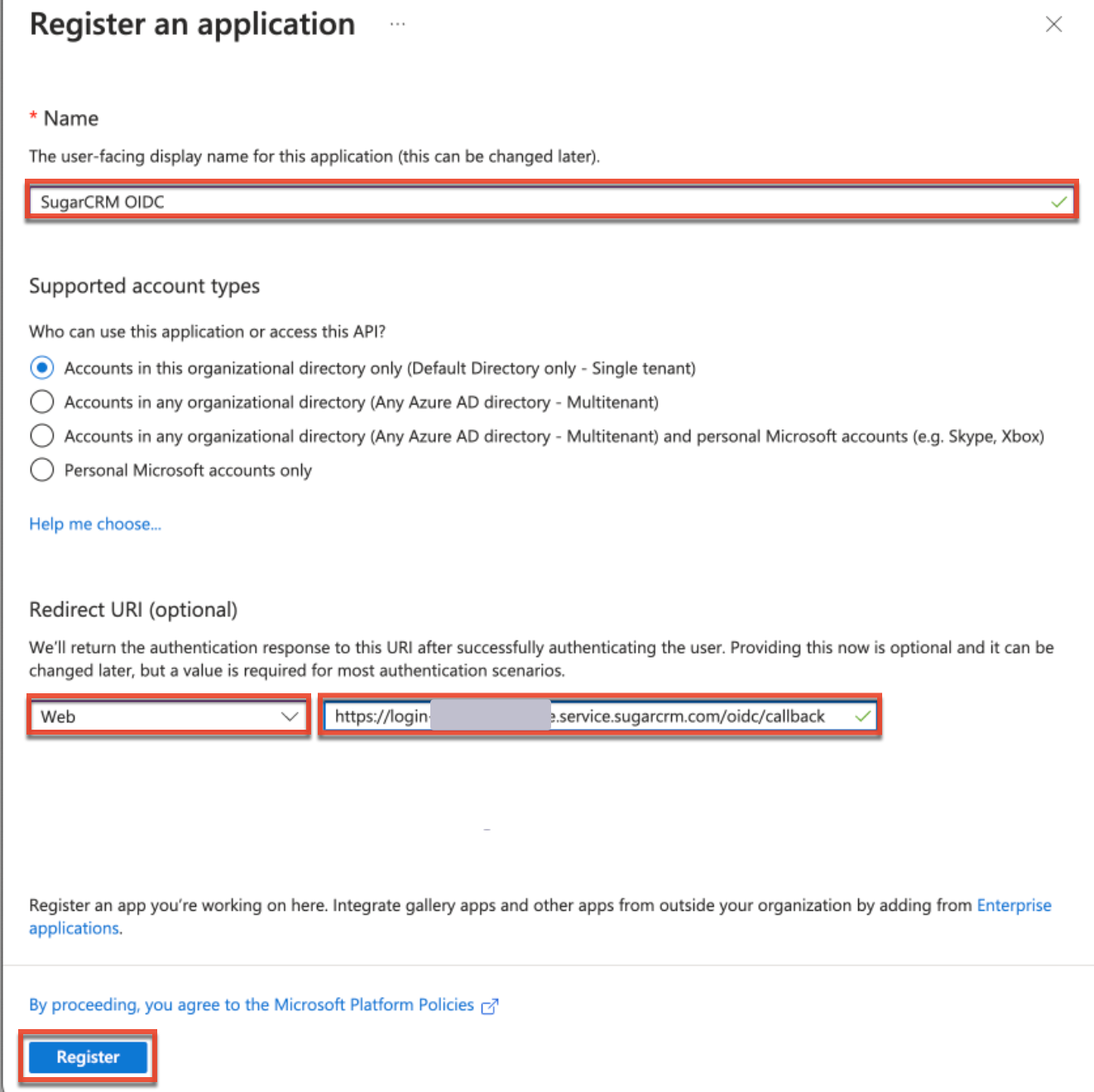
- On the Register an Application page in Azure, enter an application name of your choice (e.g., SugarCRM OIDC) then paste the Redirect URI value (obtained in step 1) into the Redirect URI field and select "Web" as the platform. Click "Register".
- Next, click "Certificates & secrets" on the left tree menu of your new application, then click "+ New client secret" in the Client Secrets section and populate the fields (e.g., Description) accordingly. Click "Add" to create the client secret.
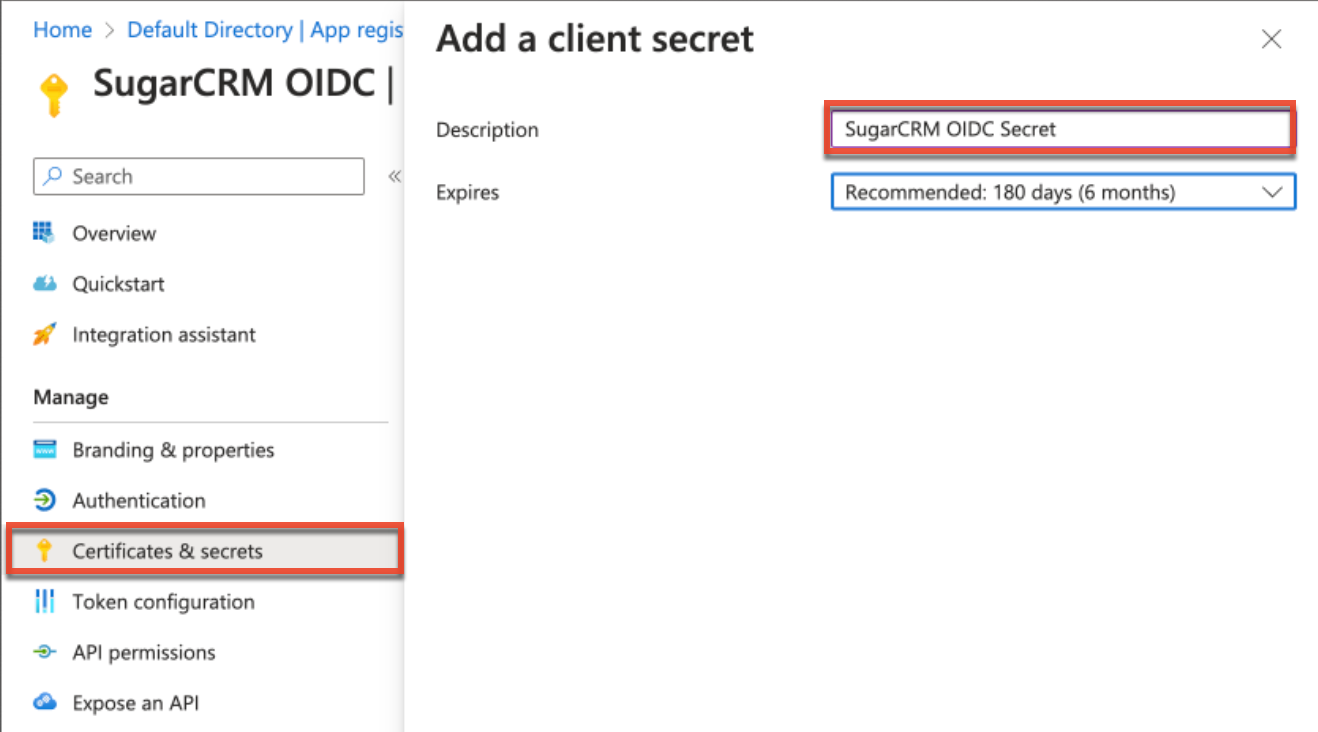
- Record the client secret value that appears under the Client Secrets section as it is required when configuring OIDC in SugarIdentity.
- Next, click "Overview" on the left tree menu and record the "Application (client) ID" value at the top of the page as it is required when configuring OIDC in SugarIdentity.
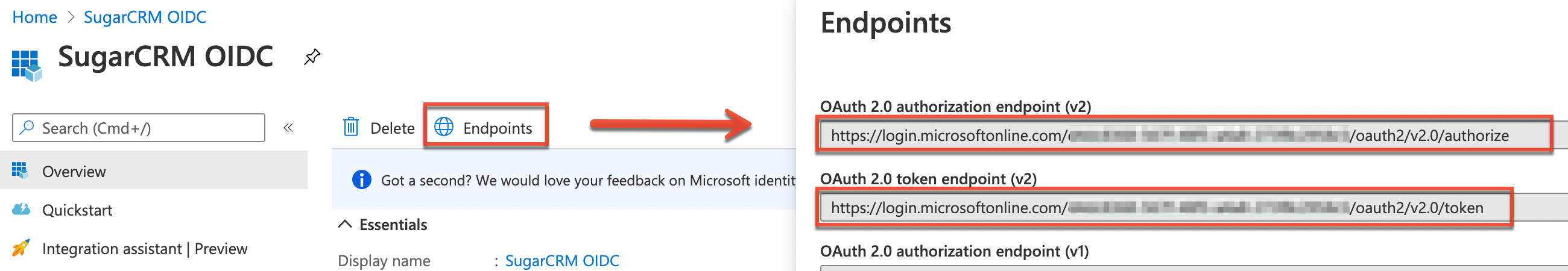
- Now, click "Endpoints" at the top of the application page and record the following Endpoint values:
- OAuth 2.0 authorization endpoint (v2): For the "OIDC Server Authentication Endpoint" field in SugarIdentity.
- OAuth 2.0 token endpoint (v2): For the "OIDC Server Token Endpoint" field in SugarIdentity.
- Finally, click "Token configuration" on the left tree menu and click the "+ Add optional claim" button. Configure the following token types:
- Select "ID", then enable the "family_name", "given_name", and "upn" claims.
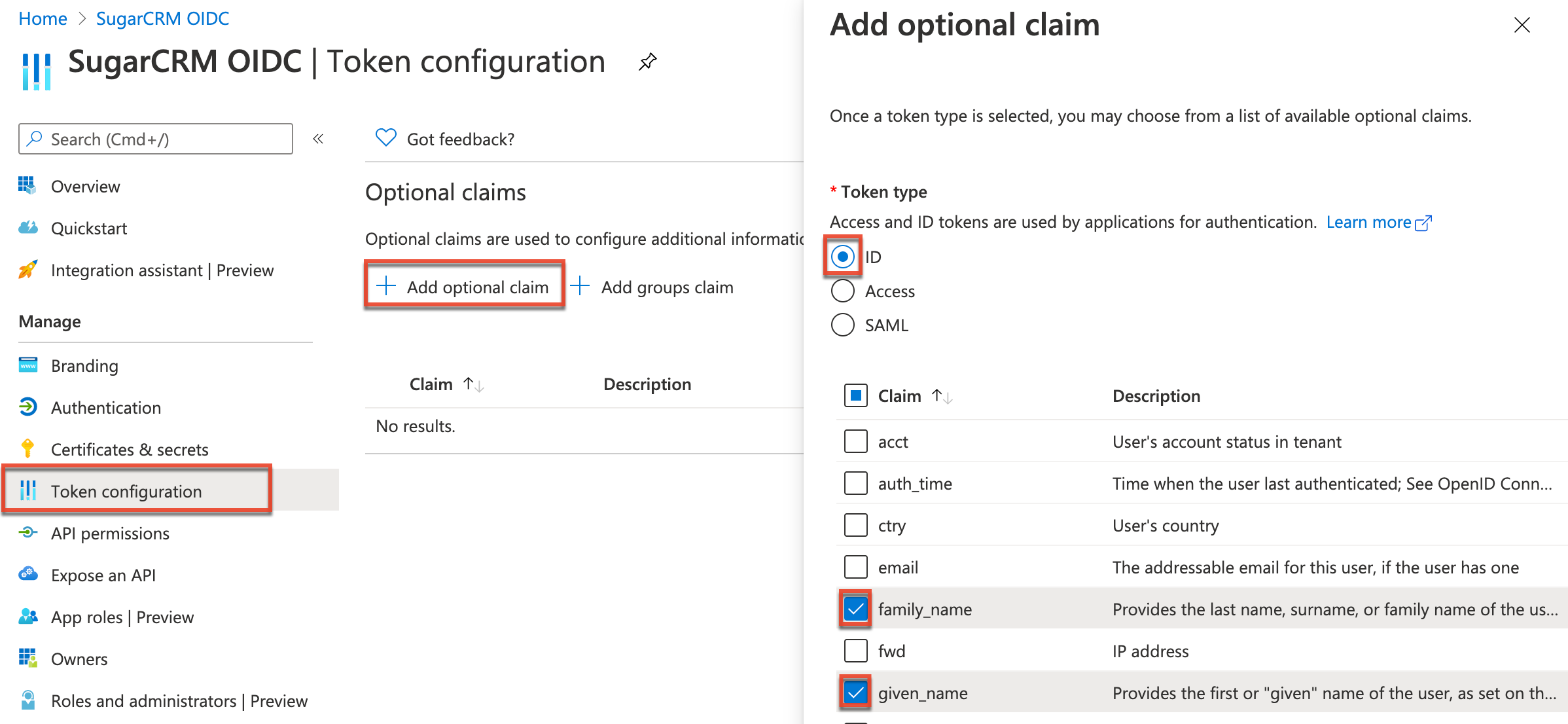
- Select "Access", then enable the "upn" claim.
- Click the Add button at the bottom of the page, then enable the "Turn on the Microsoft Graph profile permission" checkbox in the dialog box that appears.
- Select "ID", then enable the "family_name", "given_name", and "upn" claims.
Once you have obtained the necessary credentials (e.g., Client ID, Client Secret), navigate back to SugarIdentity to configure the OIDC authentication and complete the fields as follows:
- OIDC Server Authentication Endpoint: Enter the "OAuth 2.0 authorization endpoint (v2)" value from step 7 above.
- OIDC Server Token Endpoint: Enter the "OAuth 2.0 token endpoint (v2)" value from step 7 above.
- OIDC Server Userinfo Endpoint: Enter https://graph.microsoft.com/oidc/userinfo.
- Client ID: Enter the "Application (client) ID" obtained in step 6 above.
- Client Secret: Enter the Client Secret obtained in step 5 above.
- Username Attribute Mapping (optional): The "sub" OIDC attribute maps to the username field in Sugar by default. If you would like to change the attribute mapping (e.g., upn, email), you can update the Username Attribute Mapping field to select what best suits your needs.
Application
Once you have configured Azure and completed the OIDC configuration in SugarIdentity, going forward, when a user that is provisioned in SugarIdentity navigates to Sugar they will be redirected to Microsoft Azure's login page to enter their Azure credentials. Once the user's login credentials are authenticated in Azure, they will be directed back to their Sugar instance and be automatically logged in. Please note that all of the organization's users in Microsoft Azure will be assigned to the SugarCRM OIDC application by default once it has been created for SugarIdentity. For best practices on creating users in SugarIdentity, please refer to the SugarIdentity Guide.