Configuring SSO With AWS Using SAML
Overview
SugarIdentity allows single sign-on authentication using AWS and SAML so that it can be integrated with a connected system using a single user ID and password. This article walks through configuring AWS IAM Identity Center to allow external authentication using SAML 2.0 for Sugar instances that use SugarIdentity.
If you are using SugarLive in Sugar Serve, you can also set up SSO in SugarLive using SAML 2.0. To do so, you will also need to configure AWS IAM Identity Center as an identity provider for Amazon Web Services (AWS). Refer to this article on the AWS website for details on this setup.
For more information about external authentication methods, refer to the following pages:
Prerequisites
- Your organization must have an active AWS account.
- Your SugarIdentity users should be users in AWS IAM Identity Center.
- You must have access to the AWS IAM Identity Center console to complete the steps in this article.
- You must be familiar with AWS IAM Identity Center and how to set up the SSO configurations that meet your organization's needs.
- You must be a Sugar administrator to configure the SAML settings in SugarIdentity.
Steps to Complete
The following sections cover how to configure AWS IAM Identity Center to allow external authentication using SAML 2.0 for Sugar instances that use SugarIdentity.
Adding SAML 2.0 Application in AWS IAM Identity Center
- First, log in to Sugar and navigate to Admin > SugarIdentity, then click "SAML Settings" from the home page. Place a check in the Enable SAML Authentication box, then click the "Export metadata file" link in the Quick Links menu. This file will be needed in the following step.
Note: For Sugar versions 13.0 and lower, navigate to Admin > SugarCloud Settings.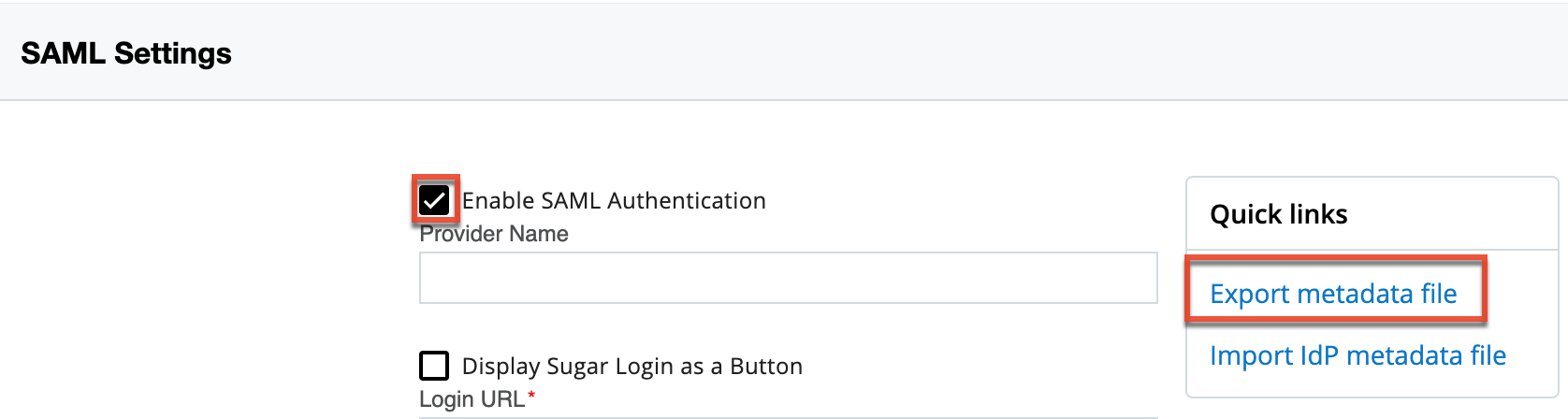
- Next, follow steps 1 - 12 in the Setting up customer managed SAML 2.0 applications page on the AWS Documentation website. Step 10 (configuring application properties in the IAM Identity Center console) can be skipped.
Note: For step 11, select the "Upload application SAML metadata file" option in the Application Metadata section and upload the metadata file that was exported from SugarIdentity in step 1. - Navigate back to the SAML Settings page in SugarIdentity and click "Import IdP metadata file" in the Quick Links menu. Select the SAML metadata file that was downloaded on step 9 of the Setting up customer managed SAML 2.0 applications page and the data (e.g., Login URL, Entity ID, X509 Certificate) it contains will instantly appear in the corresponding fields (e.g., Login URL) on the SAML Settings page. Click "Save".
Mapping Attributes for AWS IAM Identity Center
If you wish to have the attributes (e.g., First Name, Last Name) from AWS IAM Identity Center map to the SugarIdentity user fields, you will need to set up the attribute mapping in AWS IAM Identity Center. Once the attribute mapping is configured, going forward, when a new user is created in the AWS IAM Identity Center console or the user's attributes are modified in AWS IAM Identity Center, these changes will sync to SugarIdentity when the user logs in to Sugar. For more information on setting up the attribute mapping, please refer to the Configuring SAML Attribute Mapping for SugarIdentity article.
Assigning the SugarCRM App to AWS Users
In order for SugarIdentity users to leverage the AWS IAM Identity Center login capability with Sugar, you must assign the Custom SAML 2.0 app from the section above to your organization's users in AWS IAM Identity Center. For information on assigning applications to users in AWS IAM Identity Center, please refer to the Assign User Access article on the AWS Documentation website.
Application
Once you have created the application in AWS IAM Identity Center and completed the SAML configuration in SugarIdentity, going forward, when a user tries to access Sugar they will be redirected to the AWS user portal to enter their user portal login credentials. Please note that the user record must exist in SugarIdentity for the user to access their Sugar account. For more information on creating users in SugarIdentity, please refer to the User Management documentation.
Once the user's login credentials are authenticated in AWS, they will be directed back to their Sugar instance and be automatically logged in. The user can also launch their Sugar account from the AWS user portal by choosing the Custom SAML app that appears in their portal. Their Sugar instance will open in a new browser tab, and the user will be authenticated and automatically logged in.